The Play ransomware gang has taken responsibility for a cyberattack on the City of Oakland that has disrupted IT systems since mid-February.
Oakland is a city in California on the east side of the San Francisco Bay Area with a population of about 440,000. The city serves as the region’s main trace center and economic engine.
The city’s authorities informed the public it had been targeted by a ransomware attack on February 10, 2023. It impacted all network systems except 911 dispatch, fire emergency services, and the city’s financial systems.
On February 14, 2023, the City of Oakland issued a local state of emergency to expedite restoring the impacted systems and bringing all its services back online as soon as possible
All business taxation obligations received a 45-day extension, as the city couldn’t facilitate online payments. Parking citation services were also impacted, not accepting calls or transactions at cashier booths.
By February 20, 2023, IT specialists helped restore access to public computers, scanning, printing, library services, and wireless internet connectivity throughout the city’s facilities.
However, the city’s non-emergency phone services (OAK311) and the business tax licenses remained unavailable, while the online permit center returned to partial service.
The latest update on the City of Oakland website came on February 28, 2023, two weeks after the ransomware attack, with the service status remaining primarily unchanged.
Play claims responsibility for attack
The Play ransomware gang has now claimed responsibility for the attack on Oakland, listing them as victims on its extortion site on March 1, 2023, as first spotted by security researcher Dominic Alvieri.
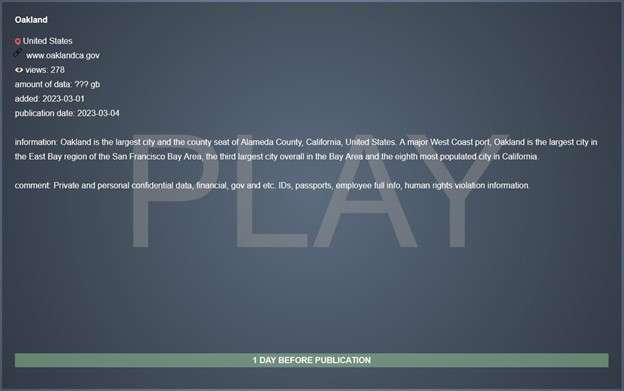
The threat actors claim to have stolen documents containing private, confidential data, financial and government papers, identity documents, passports, personal employee data, and even information allegedly proving human rights violations.
These documents were allegedly stolen during the hackers’ intrusion into the City of Oakland’s networks. They are now used as leverage to get the city’s administration to meet their demands and pay the ransom.
The threat actors threatened to publish the above documents tomorrow, so they gave Oakland roughly 72 hours to respond to the extortion.
None of the status updates published on the City of Oakland’s portal mention data exfiltration, so the city’s authorities have not yet confirmed that data was stolen.
Play ransomware launched in June 2022 when victims began disclosing attacks in the BleepingComputer forums.
Since then, the ransomware operation has attacked many organizations, including Belgium city of Antwerp, H-Hotels, Rackspace, Arnold Clark, and A10 Networks.